I hope y’all read the Week 1 article where I talked about Blockchain concepts like nodes, clients, transactions, accounts, EVM, gas fees, L2’s, ERC’s, to mention a few. This week, I will give a summary of week 2, where we dived into these concepts.
On the first day, we discussed cryptography as related to Ethereum, how keys are generated; Private keys are generated by feeding an even larger string of random bits (collected from a cryptographically secure source of randomness) into a 256-bit hash algorithm such as Keccak-256 or SHA-256, both of which will conveniently produce a 256-bit number. The 256-bit number then becomes a private key. The process of generating a private key is an offline process, not connected to Ethereum blockchain. Public keys on the other hand are calculated from the private key using elliptic curve multiplication, which is practically irreversible: K = k * G. Know that public key generation is one way, i.e you can’t use public key to generate a private key. We also discussed the Keccak-256 hashing algorithm, where the first 20 bytes of the hashed value are gotten and prefixed with “0x” to produce an Ethereum address.
On the second day, We dived into wallets. The two types of wallets; Deterministic (where the keys are generated from a random number) and Non-Deterministic wallet (where the keys are generated from a single master key known as a seed). We discussed HDW (Hierarchical Deterministic Wallets) and how it is structured in such a way that child keys are derived from parent keys and so forth. We discussed a seed known as a mnemonic phrase (BIP-44), and how when placed in a certain format, produces the private key. We discussed BIP-32 and how it is implemented to create HD wallets. We discussed the steps using BIP-39 to create mnemonic phrases. Extended public and private keys were also discussed. We also talked about how 512 bits seed is created using the mnemonic phrase
The third day was quite interesting. We discussed transactions, the components (recipient, nonce, value, input data, gas price, gas limit, (v,r,s), etc.) The Nonce was discussed further featuring its importance in the transaction executions. Transaction value and Transaction data. Transaction payment which includes having a value in the transaction. Transaction invocation where the transaction has data. Transaction invocation is mostly associated with contract's own accounts. We discussed the flow of transactions, from when there are initiated to when they are included in the Ethereum blockchain. Data payload (a hex -serialized encoding of the function selector and function arguments).
On the fourth day, we discussed digital signatures, how there are created using ECSDA (message and the sender’s private key). And how the recipient’s can verify the message using the message and public key. The three main functions of DS (are proof of ownership, proof that the message wasn’t and can’t be tempered with and that the owner of the private key can spend ether related to the “from” address.). We discussed how this digital signature is verified using the signature (r,s), the serialized transaction, and the public key related to the private key. How the recipient can confirm the sender’s address by using the public key gotten from calculating it using the ESCDA. We reference the transaction flow from when a data stricture of the transaction is created, an RLP-encoded serialize message is created, a Keccak-256 hash of the serialized message is hashed and then using ECDSA, a digital signature is created and passed alongside the message to the recipient. We also discussed the special transaction which involves a contract creation using the zero address (an address mostly used for account creation, an account that doesn't have a pair of keys, an account that contains mostly burned ethers). Note that the zero address can receive an account but can’t spend ethers. The zero address is the “to” address when creating a contract. Note that the three steps of creating a transaction, signing a transaction and broadcasting it to the Ethereum blockchain are all in one process.
On the fifth day, we followed up on transactions, we discussed transaction propagation. The Ethereum node maintains connections to at least 13 other nodes, called its neighbors. Each neighbor node validates the transaction as soon as they receive it. If they agree that it is valid, they store a copy and propagate it to all their neighbors (except the one it came from). As a result, the transaction ripples outwards from the originating node, flooding across the network till all nodes has an updated copy of the Ethereum chain after a transaction has modified it. Note that the nodes can’t tell which is the originator of a transaction (message). We discussed transaction recordings — These changes are recorded alongside the transaction, in the form of a transaction receipt, which may also include events. A transaction that has completed its journey from creation through signing by an EOA, propagation, and finally mining has changed the state of the singleton and left an indelible mark on the blockchain.
In summary, Transactions are the “inputs” that cause the Ethereum Virtual Machine to evaluate contracts, update balances, and more generally modify the state of the Ethereum blockchain.
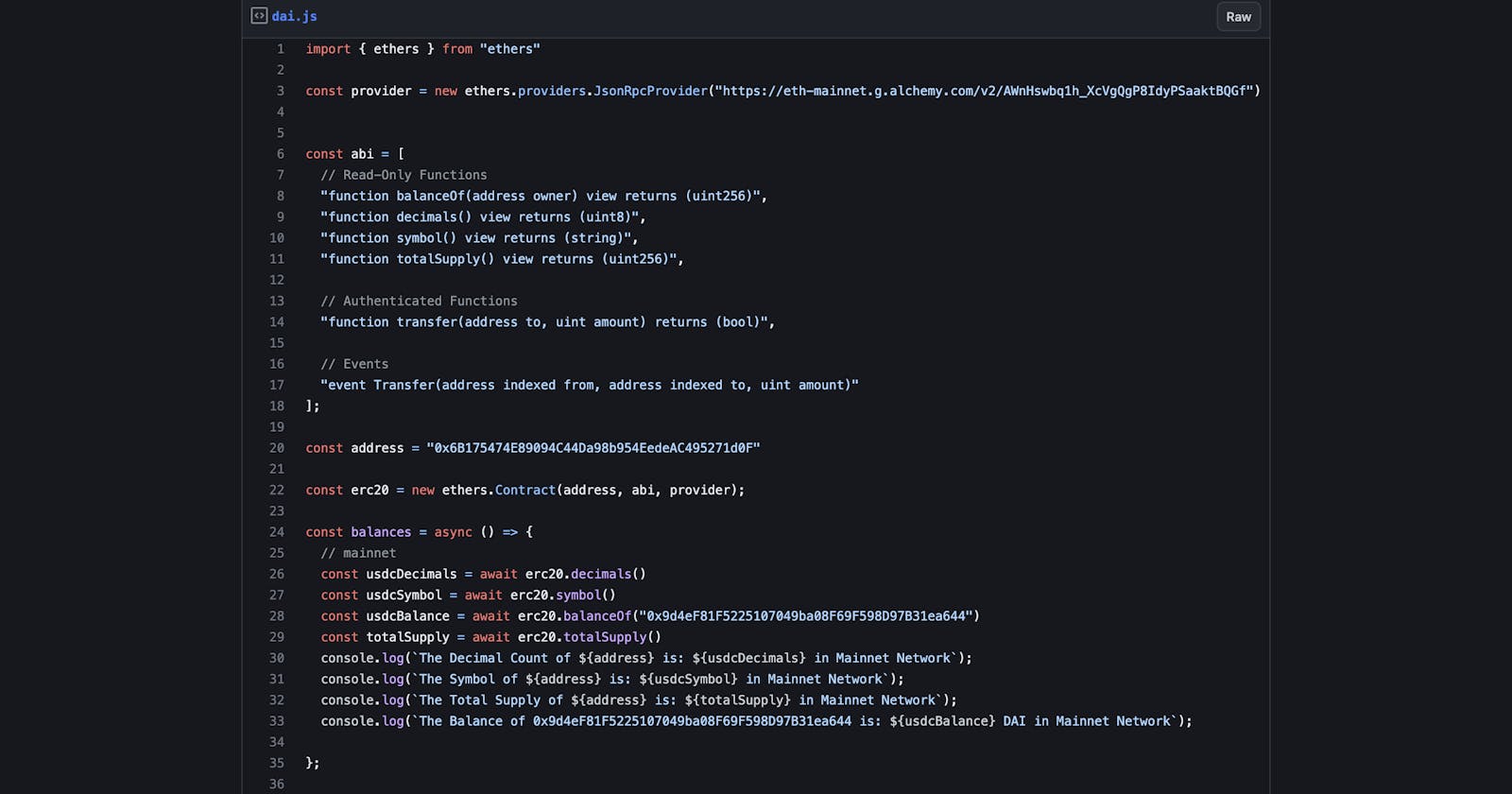
During the weekend, I used ethers library to fetch an ERC20 token symbol, total supply, decimal, and my balance using my address. here is a link to the public gist -> gist.github.com/ETIM-PAUL/b41437eddce505ef2..
I can’t wait to tell y’all about Week 3. I hope you follow through this journey with me as I progress into a Blockchain Developer.